hackthebox.eu: Bastion Walkthrough
Time for another hackthebox.eu walkthrough. This time I’ll be tackling Bastion. I’m going to try noting learning opportunities and such as I go so that I can remember what I learned and to show a light a bit on the process of learning. Also, I’ll try to note when I bounced things off of other testers I know to try and show how collaboration can help in CTFs and just penetration testing in general.
So on to the machine:
Starting off in the IppSec (https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA | https://www.patreon.com/ippsec) approved manner I ran a quick nmap with safe scripts to get the lay of the land. By the way, if you haven’t watched his videos yet… seriously get you some good process and tradecraft and give them a watch. His process and documentation are fantastic.
nmap -sC -sV -vvv --open -p- -oA bastion_scripts 10.10.10.134
This run gave me ports 22, 135, 139, 445, 5985, and some higher numbered windows RPC ports. It seems like we’ll be going after ssh and SMB on this target. So in some other HTB attempts I have learned a bit more about querying SMB from Kali Linux and know that I can use smbclient to poke around.
Ok, so there are a few things here that I don’t need to authenticate to see. I tried ADMIN$ and C$ with no luck, but did get some information from Backups. This means that I need to check around and see if there’s something I can leverage from that folder.
Parsing through this image we can see an initial folder (with a bunch of junk from other testers in it) and something that looks slightly interesting in the WindowsImageBackup folder. Once I go in there I see that L4mpje-PC has been backed up at a date that matches up with the general age of this machine. I think I’m more interested now. Then looking in that folder I find a backup directory from 2/22/2019. Looking in that folder there are a bunch of files but the most interesting are the two .vhd files.
Fellow hacker tip #1:
So I knew that I could mount these images remotely but I was banging my head against this. I tried several different methods of mount -t cifs and such and just wasn’t having any luck. I found a few things that seemed likely using forensic methods but apparently needed a bit of a push. One of my friends (thanks @m0x00) recommended this site: https://medium.com/@klockw3rk/mounting-vhd-file-on-kali-linux-through-remote-share-f2f9542c1f25 and following those directions got things mounted up just fine.
Now I could go a bit retro and grab the system hive and SAM file to work on some password cracking action.
Fortunately I was able to just copy these files from the mapped drive to my local for cracking with a cp command.
cp SAM ~/Documents/htb/bastion/ and cp SYSTEM ~/Documents/htb/bastion/
Now I can extract the hashes using samdump2. It’s pretty simple, but I did learn that the order is important. SYSTEM then SAM or it will give you an error.
So now I have a password hash that I need to crack. I frequently use John on my laptop just to see if something falls out, however I’ve been using cracking lately as a chance to learn more about hashcat. I tried that here and hoped to get success. If not, then it’s time to use the big password cracker I have access to and hope the user didn’t use a long complex password or I need to find another vector.
Success! Now that I have the password for the user L4mpje, I can see if I can use it to connect via ssh.
Access granted! Now to try to find a way to administrator level access. Back to enumeration, after grabbing the user.txt flag of course.
So nothing of interest in L4mpj3’s folders and no access to Administrator’s folders. Not much else to look for elsewhere on the drive either. We already looked in Backups and know what’s in there of interest so I guess we’ll take a look in Program Files and see what’s installed. Everything looks pretty standard in the main Program Files, but in Program Files (x86) there is a directory for mRemoteNG which is an app I’ve never heard of.
I did some initial research and it looks like you can use a Metasploit module to pull credentials if you have a shell. I will admit that I messed around with this for quite a while and read some of the comments on the HTB discussion boards and got myself confused. Eventually I figured that I needed the confCons.xml file but wasn’t sure how to get ahold of that. It certainly wasn’t where I expected it to be. After a bit more Googling for a file search command I found it.
Once I saw the location I face-palmed. Oh yeah, AppData… duh. Then I could grab this file from my mapped drive from earlier and take a look. I tried a few code solutions to recover the passwords from this file and was making things way too hard until m0x00 to the rescue again. “You have a string in the file, you should be able to get the password from that”
Fellow hacker tip #2
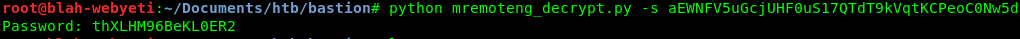
Just google for the program name and the word decrypt. This led me to the following site on github: https://github.com/kmahyyg/mremoteng-decrypt which has a super helpful python script to decrypt password strings from the confCons.xml file. So I could just grab the string and run it.
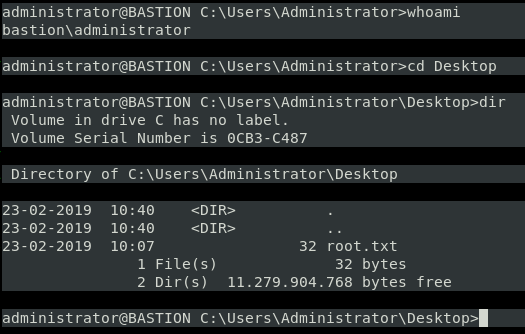
Success! So now I should have the admin password for L4mpje-PC. Let’s give it a try on ssh again.
And that’s the machine done. In this machine I learned more about smbclient and that nifty trick with mounting remote vhd files. I also reminded myself that just looking at all the information you get is important. You never know where you may find something. And the usual reminders… try simple things first and always remember that some commands like quotes around them and some don’t.